Linux File System
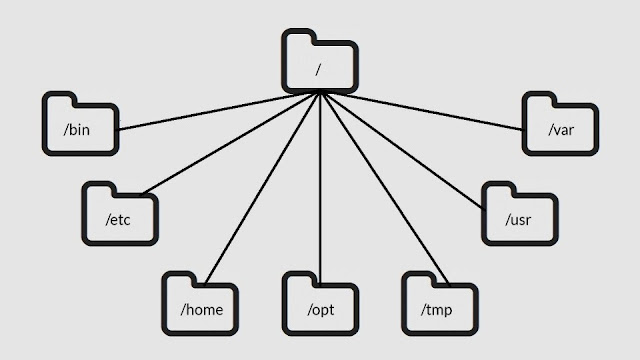
File System Linux treated everything as a file. Ever a directory is treated as a file and contains entries for several other files. All the hardware devices, such as (input/output) I/O devices, storage devices, etc. are all treated as files. The Linux file system is organised in a hierarchy which start with the root directory. The root directory is represented by forward slash (/) under the root directory there are several system directories and the name directory. /bin : - This directory contains executable program file (binary file). This directory contains all the commands of Linux in the same way as all the commands of DOS are stored in the Command.Com file. /dev : - This directory contains the special device files for example, the printer may be a file known as prn in this directory. The hard disk may be hda file and its first partition would be hda. /etc : - This directory contains all the system wise configuration information as text files. /lib : - This direc...